TrueCharts Authelia
Overview
Setup the TrueCharts Authelia application, and connect it to LDAP, on TrueNAS Scale.
Assumptions
TrueNAS Scale Setup completed.
TrueCharts Setup completed.
TrueCharts Traefik completed.
TrueCharts LLDAP completed.
Logged in as administrative user.
WARNING: TrueCharts Deprecated
TrueCharts has unfortunately been deprecated with the removal of Kubernetes from TrueNAS Scale. Consider another solution, do not start a fresh deployment of TrueCharts applications with TrueNAS Scale. Refer to the following resources for more details.
- TrueCharts. “Deprecation of TrueNAS SCALE Apps.” 2024.
- TrueNAS. “The Future of Electric Eel and Apps.” 2024.
LDAP User
Authelia needs a user account to login to the LDAP server as, create one and grant it permission to manage user passwords. Connect to the LDAP instance with the interface of choice, this section will use Light LDAP as demonstration.
After creating the user, note the username and password for use in the Authelia app configuration.
Create User
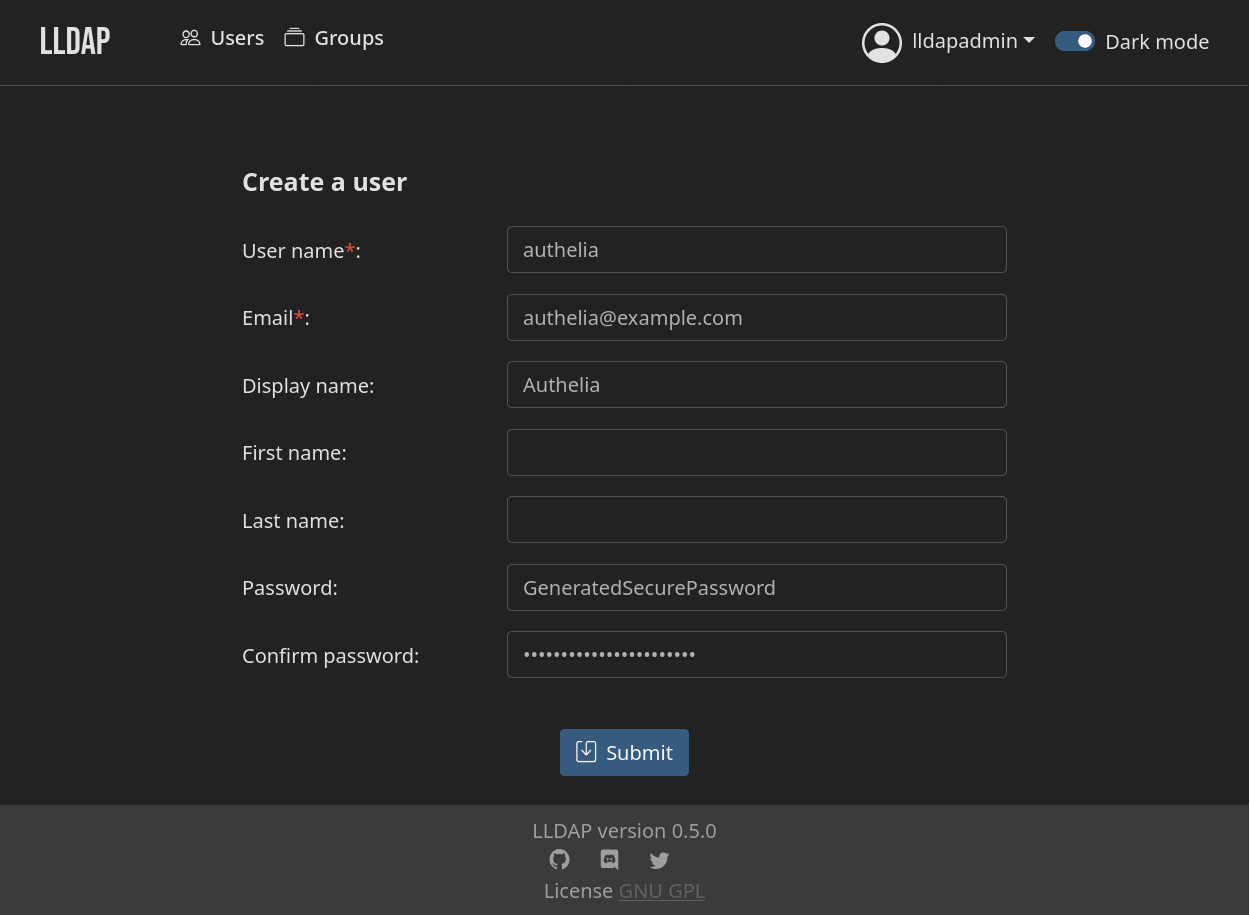
Create a new user for authelia.
| Setting | Value | Description |
|---|---|---|
| User Name | authelia | User ID for logging into the LDAP server. |
[email protected] | Email address for the user. | |
| Display Name | Authelia | Display name for user, very fancy. |
| Password | GenerateSecurePassword | Generate a secure password and save it for Authelia configuration. |
Select Submit to create the new user.
Add Group
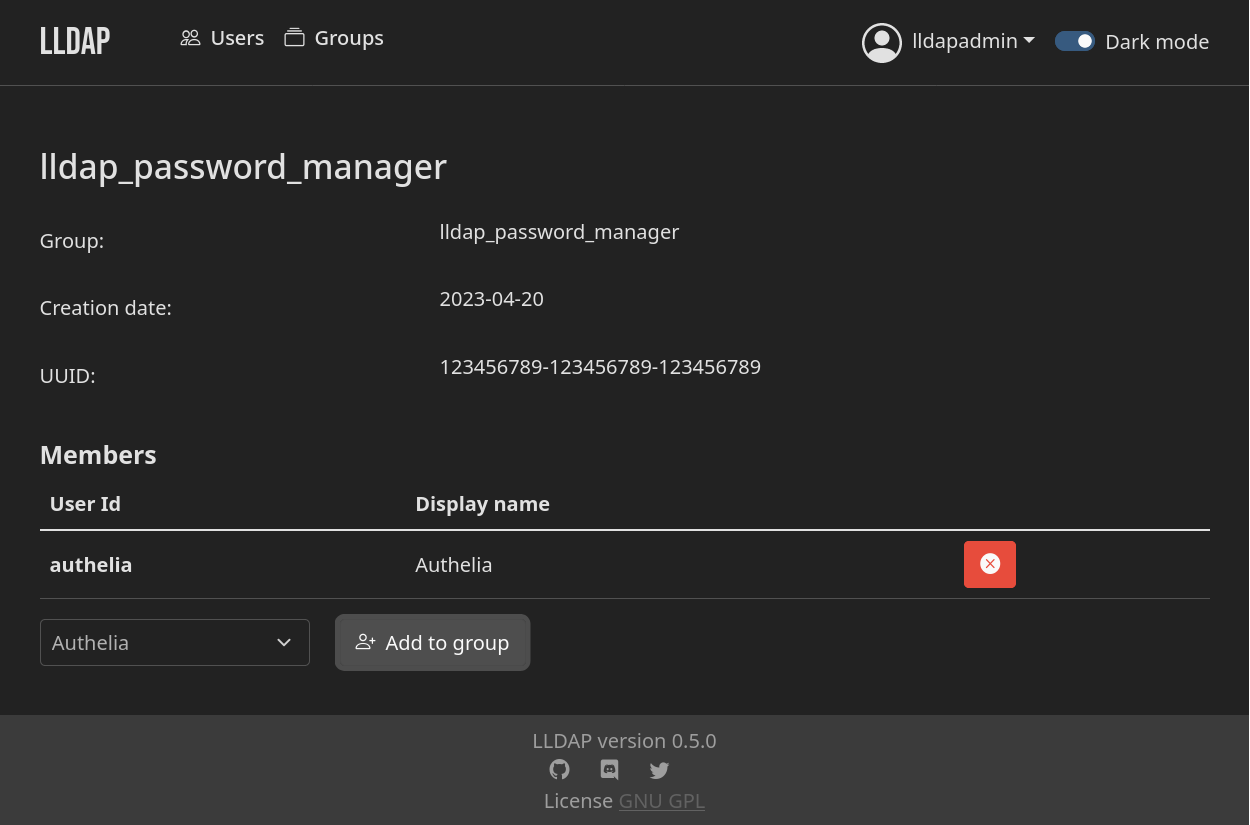
Add the new authelia user to a group that has the ability to edit user passwords. In LLDAP this can be done with the lldap_password_manager group. On other LDAP servers, use a group with read and write permissions for users.
On management interfaces like LLDAP and phpLDAPadmin, navigate to the group for Authelia. Add the authelia user as a group member.
Install Authelia
Navigate to the Applications page in the TrueNAS Scale dashboard, Apps on the main navigation.
Switch to the Available Applications tab in the Applications page.
Using the search tool, find the authelia application. Verify Authelia is from the TrueCharts catalog and is on the Enterprise train.
Select Install to begin configuration and installation of the application. Configuration options not mentioned in this section can be left as default.
Application Name
| Setting | Value | Description |
|---|---|---|
| Application Name | authelia | Name for the application. |
| Version Number | #.#.# | Version to use, latest by default. |
App Configuration
| Setting | Value | Description |
|---|---|---|
| Domain | example.com | Root domain Authelia will be providing authentication for. |
| Default Redirection URL | https://auth.example.com | Default redirect URL for authenticating with Authelia. Will be whatever ingress domain is configured for Authelia. |
| Theme | Dark | Save your eyes with the dark theme. |
Password Policy Configuration
| Setting | Value | Description |
|---|---|---|
| Enable | true | Toggle password policy. |
| Standard | false | Basic strength policy - length, case, numbers, symbols. |
| zxcvbn | true | Use zxcvbn to test password strength. |
| Min Score | 3 | Minimum required zxcvbn rating. Value from 0-4. |
Authentication Backend Provider
Connect Authelia to an LDAP server. This section will assume the use
| Setting | Value | Description |
|---|---|---|
| Disable Reset Password | false | Enable to disable password reset functionality. |
| Reset Interval | 5m | Interval to refresh data from backend. |
| LDAP Backend Configuration | true | Enable the LDAP backend. |
| Implemenetation | Custom | Use custom with Light LDAP. |
| URL | ldap://lldap-ldap.ix-lldap.svc.cluster.local:3890 | TrueNAS cluster url for LDAP server. |
| Connection Timeout | 5s | Time before giving up. |
| Start TLS | false | Enable to use StartTLS when connecting to the LDAP server. |
| TLS Server Name | | Optionally, configure server name for incorrect urls. |
| Skip Certificate Verification | false | Enable when using self-signed certs. |
| Minimum TLS Version | TLS1.2 | Minimum TLS version required for secure LDAP server connections. |
| Base DN | DC=example,DC=com | Set this to your network domain name, as configured with LLDAP. |
| Username Attribute | uid | What to use as username. |
| Additional Users DN | OU=people | Scope of users on the LDAP server. |
| Users Filter | (&(|({username_attribute}={input})({mail_attribute}={input}))(objectClass=person)) | How to filter users from the LDAP server. |
| Additional Groups DN | OU=groups | Scope of groups on the LDAP server. |
| Groups Filter | (member={dn}) | How should user groups be fetched. |
| Group Name Attribute | cn | Where to find group name. |
| Mail Attribute | mail | Attribute to use for email address. |
| Display Name Attribute | displayName | Attribute to use for display names. |
| Admin User | UID=authelia,OU=people,DC=example,DC=com | LDAP user created for Authelia. |
| Password | GenerateSecurePassword | LDAP Authelia user password generated previously. |
SMTP Provider
Setup an SMTP provider to send password reset and welcome emails to users. Refer to your email providers SMTP documentation for host, port, and app-password information.
Common email provider SMTP documentation:
| Setting | Value | Description |
|---|---|---|
| Filesystem Provider | false | Enable this when SMTP is not used. One notification provider is required for Authelia to function. |
| SMTP Provider | true | Enable to use SMTP. |
| Host | smtp.example.com | SMTP server of the provider. |
| Port | 587 | SMTP connection port. |
| Timeout | 5s | Connection timeout. |
| Username | [email protected] | Login address to use. |
| Password | ProviderAppPassword | Generate an app-password with your provider. |
| Sender | [email protected] | Email address to send email as. |
| Identifier | localhost | HELO identifier. |
| Subject | [Authelia] {title} | Email subject line {title} is dynamic. |
| Startup Check Address | [email protected] | Email address to send tests to. |
| Disable Require TLS | false | Keep it off. |
| Disable HTML Emails | true | Enable to use plain text when sending emails. |
| TLS Server Name | | Optionally, configure server name for incorrect urls. |
| Skip Certificate Verification | false | Enable when using self-signed certs. |
| Minimum TLS Version | TLS1.2 | Minimum TLS version required for SMTP connections. |
Access Control Configuration
When defining access rules manually for all applications, set default policy to deny.
| Setting | Value | Description |
|---|---|---|
| Default Policy | one_factor | Default authentication required. |
| Networks | | Optional, define networks for use within rule configuration. |
| Rules | | Different rules from the default policy for specific network elements. |
Networking and Services
| Setting | Value | Description |
|---|---|---|
| Main Service | — | — |
| Service Type | ClusterIP (Do Not Expose Ports) | Set this to cluster IP to expose Authelia via ingress. |
| Port | 9091 | Default Authelia port. |
Ingress
| Setting | Value | Description |
|---|---|---|
| Main Ingress | — | — |
| Enable Ingress | true | Use ingress for Authelia, verify ClusterIP was used for the network. |
| HostName | auth.example.com | Hostname for Authelia, use the same hostname as configured for the default redirect URL. |
| Path | / | Root path. |
| Path Type | Prefix | Prefix path. |
| Cert-Manager clusterIssuer | cert | Cluster issuer for automatic certificates. |
| Traefik Middlewares | | None, Authelia will be a middleware. |
Save
Verify you have checked the TrueCharts documentation for Authelia and Save. The application will begin installation and deploy. Navigate to the Installed Applications tab to monitor the status.
Add Traefik Middleware
Authelia Middleware
Within the Traefik application confiugration, find the Middlewares section. Add a new forward auth provider to Traefik for Authelia. The identifier Name defined here will be used when assigning this middleware to applications, auth in this example.
| Setting | Value | Description |
|---|---|---|
| forwardAuth | Add | Add a new forwardAuth provider. |
| Name | auth | Identifier when assigning this middleware to applications. |
| Address | http://authelia.ix-authelia.svc.cluster.local:9091/api/verify?rd=https://auth.example.com/ | Replace example.com with the system domain. |
| Trust Forward Header | true | Trust X-Forwarded-* headers from Authelia response. |
| TLS | - | - |
| Insecure Skip Verify | false | Leave off, disables TLS certificate validation. |
| Auth Response Headers Regex | | Regex to match headers from Authelia response. Leave blank and define authResponseHeaders. |
| authResponseHeaders | Add | Add 4 auth response headers that have the following values. Refer to the Authelia documentation on trusted headers. |
| - | Remote-User | Username of the user. |
| - | Remote-Group | Groups user is a member of. |
| - | Remote-Name | User display name. |
| - | Remote-Email | User email address. |
Save the configuration for Authelia to be added as a middleware to Traefik.
Middleware Usage
With the Authelia middleware added to Traefik, configure each application you want protected by Authelia to use the auth middleware. Open an applications configuration and find the Ingress settings.
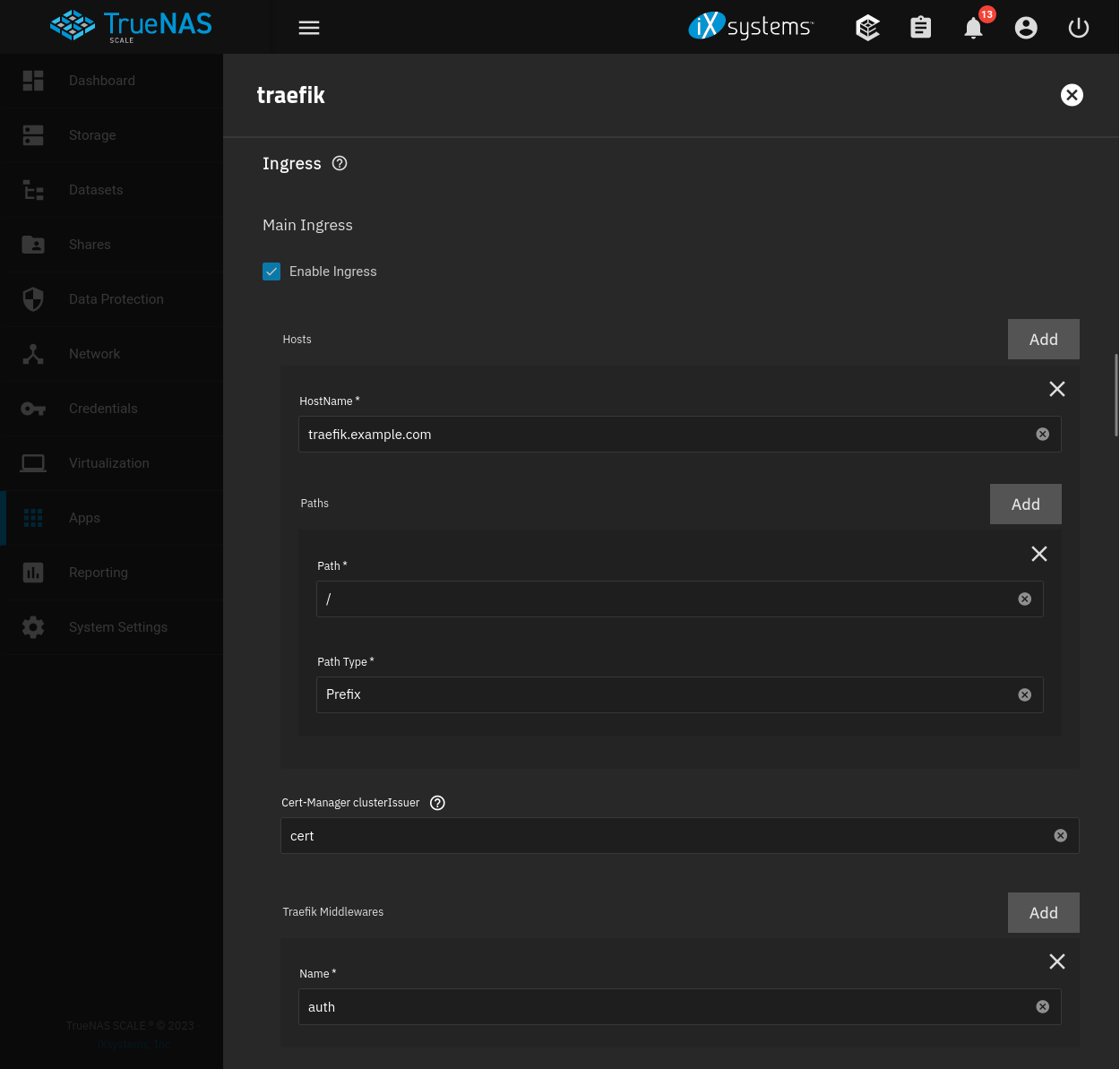
The following demonstrates Authelia as the middleware for the Traefik dashboard ingress. Authentication with Authelia will be required to access this ingress, utilizing the default policy or defined rules.
Ingress
| Setting | Value | Description |
|---|---|---|
| Main Ingress | — | — |
| Enable Ingress | true | Toggle ingress state. |
| HostName | traefik.example.com | Ingress host on the server domain. |
| Path | / | Root path. |
| Path Type | Prefix | Prefix path. |
| Cert-Manager clusterIssuer | cert | Cluster issuer for automatic certificates. |
| Traefik Middlewares | auth | Use Name identifier assigned to Authelia in the Traefik middleware setup. |
References
iXsystems. “TrueNAS Documentation.” 2025. ↩︎
TrueCharts. “TrueCharts Documentation.” 2024. ↩︎
TrueCharts. “TrueCharts GitHub.” 2024. ↩︎
TrueCharts. “Authelia Chart.” 2024. ↩︎
Authelia. “Authelia Documentation.” 2025. ↩︎
LightLDAP. “LLDAP GitHub.” 2024. ↩︎
Traefik Labs. “Traefik Documentation.” 2024. ↩︎
Traefik Labs. “Traefik GitHub.” 2024. ↩︎